Protect Your Organization, Brand, and Reputation with Email Authentication Technologies
Challenges and Goals

In the ever-evolving landscape of cybersecurity, organizations face significant challenges in ensuring robust email security, one major concern being the evolving sophistication of phishing attacks, which employ increasingly convincing social engineering tactics to trick users into disclosing sensitive information or downloading malicious content.
Also, the rise of business email compromise (BEC) attacks, where adversaries compromise legitimate email accounts to conduct fraudulent activities or unauthorized transactions, poses a substantial threat. As remote work becomes more prevalent, the expanded attack surface and the reliance on personal devices for email access introduce vulnerabilities. Furthermore, the persistence of email domain spoofing and the difficulty in fully eliminating false positives in spam detection contribute to the complex landscape of email security, requiring a multifaceted approach to safeguard against diverse and continually evolving threats. Finally, cultivating brand recognition also emerges as a strategic imperative for organizations.
What Is Android Management API?
Organizations can implement various security measures to combat phishing, enhance email trust, and overall ensure that their email messages are legitimate. Let’s have a deeper look into all the email authentication protocols, methods, and standards currently available and use by internet service providers (ISPs) to detect and present spam, as well as phishing attacks, helping protect organizations against cybersecurity attacks relying on emails.

Limitations and Vulnerabilities
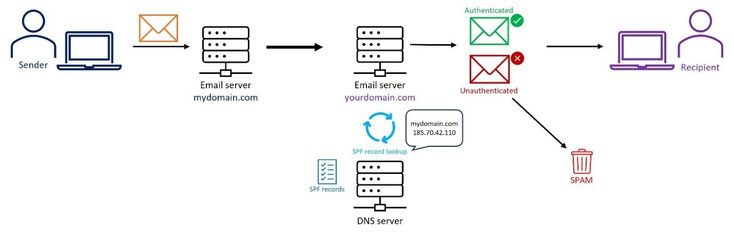
SPF is an email authentication protocol that helps prevent email spoofing and phishing by allowing email domain owners to specify which mail servers are authorized to send emails on their behalf. Email receivers can check incoming emails against the SPF records, published by the sending domain on Domain Name Servers (DNS), to verify their authenticity.

If the incoming email server finds that the email was sent from an authorized server, it is more likely to accept the message; otherwise, the message will be discarded, and eventually end up in the recipient’s Spam folder.
Challenges
SPF is one of the methods used in email authentication to combat spam and phishing, enhancing email security and trustworthiness, however it has its own limitations. First, while SPF addresses the issue of email authentication, it does not provide encryption for the content of email messages, so it only helps verify the source of an email but does not actually ensure the confidentiality of the email content.
Plus, it has a limited authorization scope, as it only helps validate the sender’s address in the Return-Path (also known as “Mail from”) field of the email header, that users can see in their email clients, but can easily be forged.
Another drawback of SPF is its limited effectiveness with forwarded emails, as the sending mail server usually substitutes the original sender's email address in the Return-Path field with the forwarder's address, and the receiving server will verify the SPF record of the forwarder's domain; in such cases, the message is expected to successfully pass SPF. However, not every email platform alters the Return-Path field during forwarding, and if so, the message will not pass SPF.
Finally, its effectiveness relies on the correct configuration of records in the DNS, which can be misconfigured or become outdated, leading to false positives or false negatives in email authentication. Managing SPF records can become complex for large organizations with multiple mail servers and third-party services sending emails on their behalf, requiring proper maintenance effort to ensure that legitimate sources are properly authorized.
Actions for the Administrators
DKIM is an open standard for email authentication that helps verify the authenticity and integrity of email messages using asymmetric cryptographic keys. When an email is sent with DKIM, the sending mail server adds a digital signature to the message header, which is generated using a private key held by the sender. The recipient's email server can then use a public key published in the sender's DNS records to verify the DKIM signature. If the signature is valid, it confirms that the email hasn't been altered in transit and that it was indeed sent by the claimed sender. Note that this is usually not visible at the end-user’s level, as all the validation work is performed at the server level. DKIM helps prevent email spoofing, phishing, and tampering, improving email security and trustworthiness.

Challenges
While DKIM helps verify the authenticity of the sender, it doesn't prevent the creation of new emails with different DKIM signatures, leaving room for malicious actors to send deceptive emails that appear to be from a legitimate domain. Also, as SPF, DKIM relies on DNS for key storage, so misconfigurations in DNS records or compromission of private keys can compromise its effectiveness in ensuring the authenticity of emails. Finally, DKIM signatures may break when emails are forwarded or modified during transit, presenting challenges in environments where emails are frequently forwarded, potentially impacting the reliability of its verification.
Effective management and rotation of cryptographic keys also pose complexity, especially for large organizations with multiple mail servers, so maintaining robust key management practices is crucial for the security and effectiveness of DKIM, which only focuses on authenticating the email's origin and does not encrypt the content, and by doing so does not ensure the confidentiality of the email's message either.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
While DKIM helps verify the authenticity of the sender, it doesn't prevent the creation of new emails with different DKIM signatures, leaving room for malicious actors to send deceptive emails that appear to be from a legitimate domain. Also, as SPF, DKIM relies on DNS for key storage, so misconfigurations in DNS records or compromission of private keys can compromise its effectiveness in ensuring the authenticity of emails. Finally, DKIM signatures may break when emails are forwarded or modified during transit, presenting challenges in environments where emails are frequently forwarded, potentially impacting the reliability of its verification.
Effective management and rotation of cryptographic keys also pose complexity, especially for large organizations with multiple mail servers, so maintaining robust key management practices is crucial for the security and effectiveness of DKIM, which only focuses on authenticating the email's origin and does not encrypt the content, and by doing so does not ensure the confidentiality of the email's message either.

The recipient's email server receives the email and checks SPF and DKIM records, then checks the DMARC policy for the sender's domain. If the authentication passes and aligns with the "From" domain, the email is delivered according to the DMARC policy. If not, the DMARC policy instructs the recipient's server on how to handle the email.
DMARC has three main policy options:
a) “None” policy, also referred to as “monitor” policy, takes no action, and is recommended to start with, as part of the learning process, to monitor suspicious activities while allowing legitimate traffic.
b) “Quarantine” policy instructs to sends unauthorized emails into a separate folder, but is not actively protecting yet from potential threats, simply categorizing them as such.
c) “Reject” policy blocks any unauthorized emails so that they cannot reach recipients, actively protecting from potential threats. Also, forensic reports are sent to the domain owner, providing insights into email authentication results and potential abuse.

By implementing DMARC, domain owners can better protect their domains from email spoofing, phishing, and other malicious activities, while also gaining visibility through the reporting mechanisms provided by DMARC.
While DMARC protocol can help protect against spoofing and/or phishing attacks, it can be difficult to implement and later time-consuming to maintain, without using specific tools and with the proper level of expertise required for the task
Authentication Received Chain (ARC)
ARC is an email authentication standard designed to address issues related to the forwarding of emails and the preservation of authentication results as emails are relayed through intermediary mail servers, extending existing email authentication standards like SPF, DKIM, and DMARC.
While DMARC assumes that are sent directly from sender to recipient unchanged, there still are some legitimate situations where email content might be modified during its journey:
- When forwarding an email, the person forwarding it might edit the original content (add/remove information for privacy), or the mail server might change the email header.
- When sending an email via a mailing list, it may add the list name to the Subject line, or a typical “Unsubscribe” link or disclaimer in the message footer.
This would result in legitimate emails to be detected as potentially having been tampered with, so they would fail DKIM checks. Same as email messages sent from a new/different IP address (ex: new email server implemented by sending domain) would automatically fail SPF validation tests. If both SPF and DKIM fail, DMARC fails and so email messages are rejected or treated as SPAM.
ARC addresses that by adding new email headers, such as ARC-Authentication-Results (AAR), ARC-Message-Signature (AMS) and ARC-Seal (AS), containing authentication information from each hop along the email route/journey, allowing the final recipient's email server to verify authentication results from previous stages, ensuring the email's integrity and origin, even after it has gone through multiple intermediaries, enhancing email security, particularly in forwarding scenarios.

ARC can help ensure that forwarding does not negatively impact DMARC authentication results, enhancing the overall effectiveness of DMARC policies.
Challenges
But same as with previous standards and protocols, ARC also has its own limitations. First, it depends on intermediaries to preserve authentication, risking breakdowns if servers lack ARC support. While intended to maintain authentication through forwarding, it doesn't offer end-to-end verification like DKIM. Also, adoption remains limited, hindering its impact. Plus, if an intermediary is compromised, it could potentially manipulate authentication results, posing security concerns. Additionally, it adds complexity to email servers and relies on broad industry acceptance for effectiveness. Finally, some email clients may not fully interpret or display ARC information, affecting its utility in enhancing end-user understanding of email authenticity.
Brand Indicators for Message Identification (BIMI)
BIMI is an email authentication and marketing protocol that allows email senders to display their brand logos alongside their email messages in the recipient's inbox, helping in enhancing email trust and security by providing a visual indicator of a legitimate sender, making it easier for recipients to identify genuine emails. To use BIMI, senders must have strong email authentication mechanisms in place, such as DMARC, SPF, and DKIM to verify their legitimacy, benefiting both senders and recipients by reducing phishing risks and improving brand recognition in email communications.
Verified Mark Certificates (VMC) are used to authenticate brand logos and confirm ownership of those logos. Incorporated within a BIMI record, VMC digital certificates empowers senders to present their company's logo directly alongside email messages within the user’s inbox, with providers like Apple, Google, or Yahoo, to name a few.
BIMI and VMC work together as follows: VMC validate BIMI records through a process where the email server first checks the specified logo URL for validity. If the URL is valid, the server then verifies the logo's association with the VMC, ensuring that the certificate authenticates the published logo. Upon successful verification, the email server accepts the logo and displays it next to the message in the recipient's inbox.

This visual trust element enhances email security, helping users identify and trust legitimate emails, ultimately mitigating phishing risks and improving overall email authenticity.

Limitations
While BIMI is gaining adoption in email marketing and cybersecurity efforts as an emerging standard, it is still under development, and so not universally supported by all email clients yet. However, as more email providers and organizations implement BIMI, it has the potential to become a valuable tool in the fight against email phishing and fraud.
To implement BIMI, organizations need to follow the specifications outlined by the BIMI working group, ensure proper email authentication through DMARC, and publish a valid BIMI record in their DNS (Domain Name System) settings.
SPF, DKIM, and DMARC are core email authentication protocols that work together to authenticate email senders and prevent phishing, while BIMI complements these protocols by enhancing the visual representation of the sender's brand within email messages, improving both email security and brand recognition.
Availability
While many enterprise-level email platforms support most, if not all the previously discussed email authentication protocols, it is important to keep in mind that the availability of specific features and capabilities may vary. Most cloud-based, enterprise messaging service like Microsoft Exchange Online or Google Workspace, do provide native support for these protocols, while for on-premises solutions it usually requires the use of third-party solutions, either deployed in front of the messaging environment, or directly into the environment in the form of plugins or other forms of integrations.
Conclusion
In the ever-evolving landscape of cybersecurity, safeguarding your organization from the perils of spoofing and phishing attacks is paramount. These malicious activities, aiming to deceive by falsifying identities or tricking individuals into divulging sensitive information, pose significant threats to data integrity and organizational reputation. Ensuring the seamless flow of legitimate email traffic is crucial for effective communication. By implementing technologies like SPF and DKIM, organizations can authenticate and validate their outbound emails, enhancing reliability and mitigating the risk of being erroneously flagged as spam.
To fortify defenses further, robust email authentication mechanisms such as DMARC and ARC should also be employed, alongside comprehensive employee training to recognize and report phishing attempts.
Finally, cultivating brand recognition through BIMI protocol allows companies to display their logos next to authenticated emails in supported email clients, enhancing brand visibility and authenticity in email communications, as the presence of a recognizable logo lends credibility to emails, helping recipients quickly identify legitimate messages and reducing the risk of falling victim to phishing attacks. This visual authentication not only reinforces brand trust but also contributes to a consistent and professional brand image. As email remains a primary mode of communication for businesses, utilizing BIMI becomes a valuable tool in establishing and reinforcing brand identity, ultimately improving customer confidence and engagement.
The right permutation of solutions and protocols is always going to be difficult, but ISEC7 can help you scale with the growth of your email demands. Please feel free to contact the team at ISEC7, and we can provide an objective assessment of what can address the needs of your organization and help you navigate the best options available to you.
